Going through this guide
I’m able to ssh and everything but my dashboard is blocked out now. What port needs to stay open in order to view your dashboard/rutorrent etc.
Thank you!

Going through this guide
I’m able to ssh and everything but my dashboard is blocked out now. What port needs to stay open in order to view your dashboard/rutorrent etc.
Thank you!
443(https)
If you don’t already know iptables then UFW is way easier and I would highly recommend it. Its a front end to iptables.
Thanks for response. I’d prefer to just learn IPTables but of course I’m stuck again.
I got the dashboard working.
Do you happen to know the ports for rutorrent/rtorrent and Deluged ?
The port for Deluged is dependent on whatever is generated on install (this is a randomized process). If you click the deluge link on your dashboard within your menu, you will see the deluge port attached to the URL in your browser.
RUTorrent much like the dashboard uses standard wen ports, so (80,443). You will additionally need to look to your scgi mount ports as well. This can be seen within your rtorrent.rc folder that is located in your /home/_username_/ directory.
I assume he/she’s looking for the incoming torrent traffic. In rutorrent mine is set to randomly pick a port range for incoming traffic. You’ll need to uncheck that in the rutorrent gui and specify a port range and then open that range in the firewall. I’m not sure on how deluge picks its listen range.
Thank you both! What great support
Right, I typically allow all and all block certain ‘known’ ranges. Much easier. However, I also tend just leave it alone these days as having a seedbox targeted is a rare occurrence… unless you have “friends” that want what you got.
Could you be more specific where to find the scgi mount ports. I have been guessing trying to figure out how to open this file with no luck.
would I do something like
sudo nano /home/username/rtorrent.rc/.rtorrent.rc
thanks!
Agreed. I leave it open except for specific ranges(most of the 1024 and below) and thats just to keep my logs cleaner.
Seedboxes are disposable in my opinion. Wipe and replace…switch companies and replace. There is little on there than would cause issues if it got hacked. Oh well, wipe and replace…under 2 hours and I’m back in business.
I like quickbox because I can do that with little effort and get the same results each time. Your updating system is awesome. Very well done.
We should flesh out the security section…tutorials on setting up passwordless access, using UFW if desired.
I tend to use some HIDS on all of my boxes out of habit…tripwire for home/seedboxes and commercial for work.
nano /home/Username/.rtorrent.rc
that will give you the config for rutorrent
Agreed. I have something in the works at the moment that will essentially build ssh keys within the sudoers ~/.ssh directory and import them to the authorized_keys file. Then supply an archive zip package link for download. Then they can connect without-password to their system with ease.
I may have this done by the middle of this week… Thursday possibly. However, there is a lot that should be specified in our security directory… especially so people understand these processes… another of which would be fail2ban templates that are actually friendly to use with a seedbox. These essentially do exactly as you say, just block lower ranges and call it a day. Maybe I’ll add the ability (another widget) that reads the access logs - etc from the dashboard, then the user can review these - see the space they tend to take up - and delete them with a click when ready.
We’ll see.
that wont give him the scgi port though. He’d need to look at /etc/apache2/sites-enabled/default-ssl.conf
I still need to implement your other suggestion. Just having these piped to a local db.dump file for reading on the users dashboard will be a huge help in these cases.
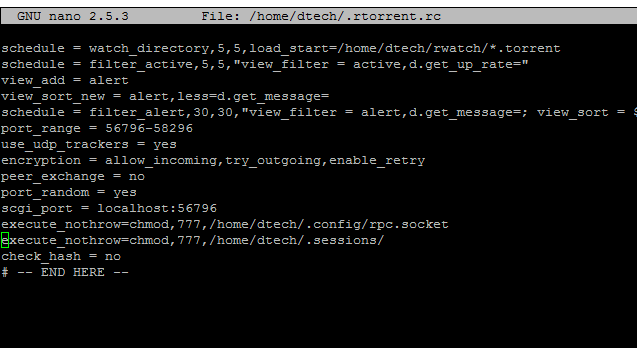
it will give him the port used towards the bottom.
you’re right. Sorry. Same info, easier way to get it.
I think you need to get a mail system on these boxes. Set it up via the gui to forward it out to gmail, etc. In my opinion, its going to be needed long term for things like logs, update notifications, etc. most ‘apps’ like couchpotato, sonarr, etc have their own email setup however you’ll need one for quickbox itself.
Yes, I was thinking about just putting in postfix/sendmail and then inserting the users desired email as the delivery for root in aliases, i.e;
mailer-daemon: postmaster
postmaster: root
nobody: root
hostmaster: root
usenet: root
news: root
webmaster: root
www: root
ftp: root
abuse: root
root: [email protected]
This method also would make for a much easier Firewall integration as well, like CSF which is already an install-able package. It just needs to have some work done to it. It will be another option in the Package Management Center and can be enabled/disabled via toggles.
I just added a vote to this:
I wanted to setup ufw and wanted to know if things have got any simpler, I have installed it and enabled it and of course was locked out of quickbox screen, I added exclusion for port 4747 which worked but my ip address changes all the time so adding ip address not much good for me do I really need to find out port for rutorrent, plex etc?
Nope, same old UFW doing it’s same old shenanigans.
Instead of UFW, you can uninstall that and use the included CSF for iptables management and it’s much easier to use with an included GUI. If you’re not too familiar with iptables I wouldn’t mess with them too much as this is known to happen all too often… in loads of web applications.
If you can manage to get back on your server I would simply remove ufw with sudo ufw disable and then remove it with sudo apt-get remove ufw.
Next, install CSF with box install csf
The good thing with CSF as opposed to UFW is that CSF is included in the QuickBox Eco-System and in turn, it is better supported. If you notice anything off with CSF or some settings that may render an app crippled… just shout out here in the plaza and settings to the CSF configuration can be adjusted accordingly. By default CSF is already setup to allow specific port ranges for the included applications.