https://www.reddit.com/r/seedboxes/comments/82184a/psa_severe_quickbox_vulnerability/ !
One key point is this… it’s the disclaimer on the README that states:
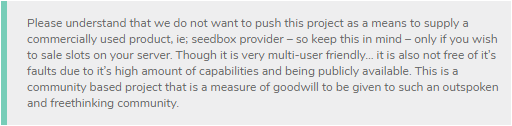
Update:
Ok, I was able to replicate this and I now know where to patch to remove this. Keep in mind, LShell was not packaged to ensure a positive jail on users… it is merely a limited shell as the name implies. As QuickBox was built to share with trusted users, not to resell to the masses.
I am working on a patch for this now.
Here you go:
Note that the sed string is no longer necessary for QuickBox to perform many of it’s UI functions. I am going to comb through and remove additional sets that may not be in use anymore as there are some relics leftover from versions used… long ago.
I am going to keep playing with it and if anyone else is tempted to test this theory, I’d be highly interested in your experiences.
And another:
About this one:
This command can be used in conjunction with system() function executions to additionally gain root access.
Thanks to /u/MrBaconwitz @ reddit for pointing this one out!
And another:
About this one:
For existing installs, modify your /etc/sudoers file. Comment or completely remove the following:
%www-data ALL = (ALL) NOPASSWD: CLEANMEM, SYSCMNDS, PLUGINCMNDS, PACKAGECMNDS, GENERALCMNDS
www-data group does not need specific permissions. Functions should be fired by user accounts.
Thanks to @liza / @liaralabs for the continued suggestions per security 
Sorry kinda worded it wrong… just wanted to bring it to your attention
No worries and I appreciate you posting this. I have pushed a commit to address this issue as above and have tested. The vulnerability is now dead. 
At least in this format. I will be testing other possibilities throughout the day.


